This is a walkthrough for “Enumerating Active Directory” of TryHackMe
Task2
Q1. What native Windows binary allows us to inject credentials legitimately into memory?
A. runas.exe
Q2. What parameter option of the runas binary will ensure that the injected credentials are used for all network connections?
A. /netonly
Q3. What network folder on a domain controller is accessible by any authenticated AD account and stores GPO information?
A. SYSVOL
Q4. When performing dir \za.tryhackme.com\SYSVOL, what type of authentication is performed by default?
A. Kerberos Authentication
Task3
Q1. How many Computer objects are part of the Servers OU?
Hint. Use MMC and navigate to the Servers OU
Follow the steps mentioned in TryHackMe to set up MMC.
ServersVerify the OU.
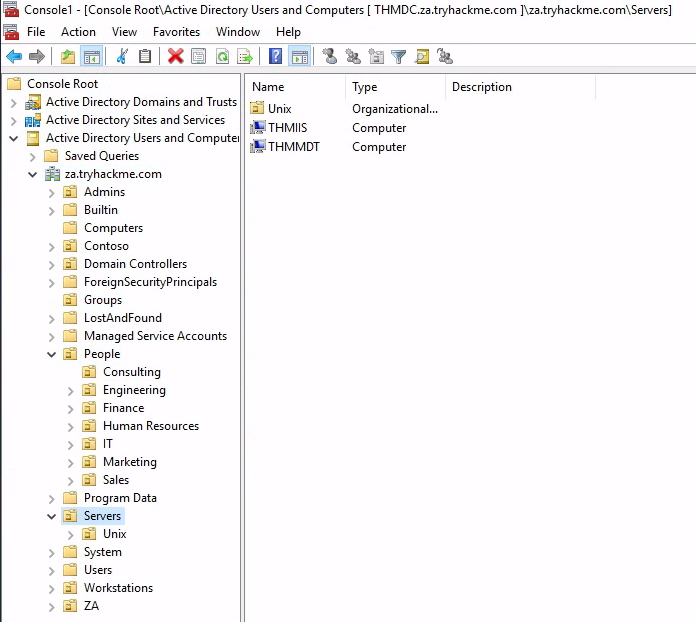
A. 2
Q2. How many Computer objects are part of the Workstations OU?
WorkstationsVerify the OU.

A. 1
Q3. How many departments (Organisational Units) does this organisation consist of?
Hint. Look under the People OU for department OUs.
PeopleCheck the subordinates.
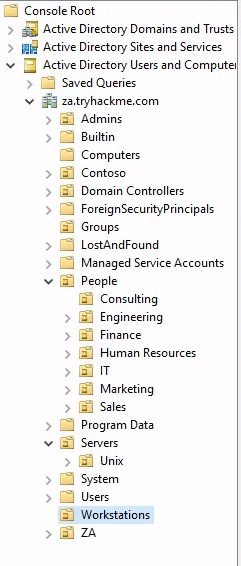
A. 7
Q4. How many Admin tiers does this organisation have?
Hint. Look under the Admin OU for tier OUs.
AdminsVerify the OU.

A. 3
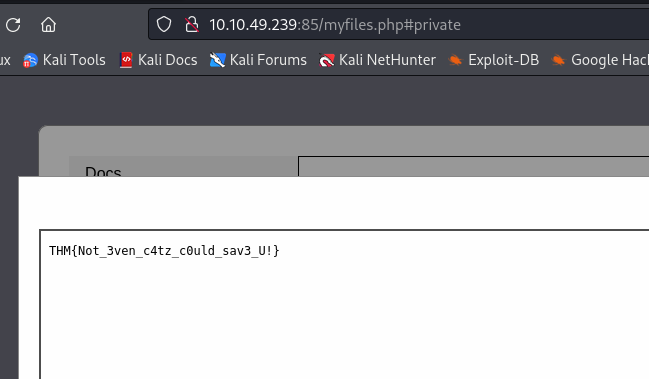
Q5. What is the value of the flag stored in the description attribute of the t0_tinus.green account?
Find Users, Contacts, and GroupsSearch for the account from and check the flags.t0_tinus.greenDescription

A. THM{Enumerating.Via.MMC}
Task4
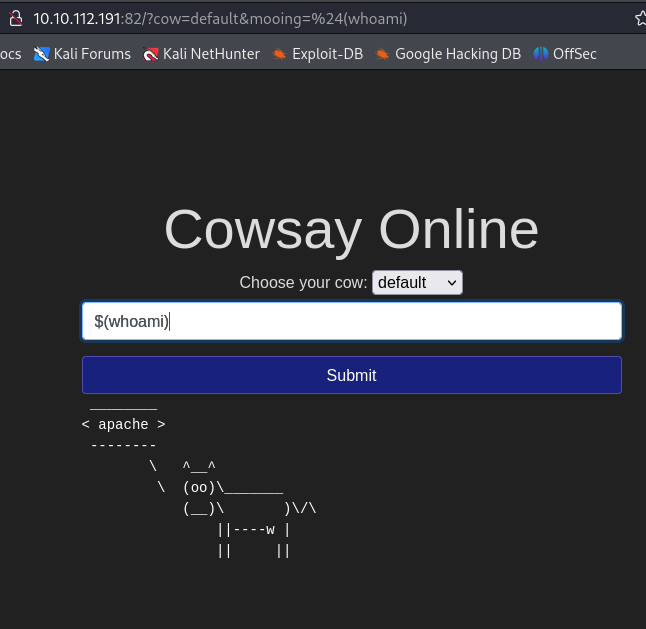
Q1. Apart from the Domain Users group, what other group is the aaron.harris account a member of?
aaron.harrisView the account details and review the items.Global Group memberships
za\david.cook@THMJMP1 C:\Users\david.cook>net user aaron.harris /domain
The request will be processed at a domain controller for domain za.tryhackme.com.
User name aaron.harris
Full Name Aaron Harris
Comment
User's comment
Country/region code 000 (System Default)
Account active Yes
Account expires Never
Password last set 2/24/2022 10:05:11 PM
Password expires Never
Password changeable 2/24/2022 10:05:11 PM
Password required Yes
User may change password Yes
Workstations allowed All
Logon script
User profile
Home directory
Last logon Never
Logon hours allowed All
Local Group Memberships
Global Group memberships *Domain Users *Internet Access
The command completed successfully.
A. Internet Access
Q2. Is the Guest account active? (Yay,Nay)
GuestView the account details and review the items.Account active
za\david.cook@THMJMP1 C:\Users\david.cook>net user Guest /domain
The request will be processed at a domain controller for domain za.tryhackme.com.
User name Guest
Full Name
Comment Built-in account for guest access to the computer/domain
User's comment
Country/region code 000 (System Default)
Account active No
Account expires Never
Password last set 1/31/2025 2:47:20 PM
Password expires Never
Password changeable 1/31/2025 2:47:20 PM
Password required No
User may change password Yes
Workstations allowed All
Logon script
User profile
Home directory
Last logon Never
Logon hours allowed All
Local Group Memberships *Guests
Global Group memberships *Domain Guests
The command completed successfully.
A. Nay
Q3. How many accounts are a member of the Tier 1 Admins group?
Tier 1 AdminsReview the details of the group.
za\david.cook@THMJMP1 C:\Users\david.cook>net group "Tier 1 Admins" /domain
The request will be processed at a domain controller for domain za.tryhackme.com.
Group name Tier 1 Admins
Comment
Members
-------------------------------------------------------------------------------
t1_arthur.tyler t1_gary.moss t1_henry.miller
t1_jill.wallis t1_joel.stephenson t1_marian.yates
t1_rosie.bryant
The command completed successfully.
A. 7
Q4. What is the account lockout duration of the current password policy in minutes?
View the password policy and review the items.Lockout duration
za\david.cook@THMJMP1 C:\Users\david.cook>net accounts /domain
The request will be processed at a domain controller for domain za.tryhackme.com.
Force user logoff how long after time expires?: Never
Minimum password age (days): 0
Maximum password age (days): Unlimited
Minimum password length: 0
Length of password history maintained: None
Lockout threshold: Never
Lockout duration (minutes): 30
Lockout observation window (minutes): 30
Computer role: PRIMARY
The command completed successfully.
A. 30
Task5
Q1. What is the value of the Title attribute of Beth Nolan (beth.nolan)?
Hint. Use Get-ADUser, remember to set -Properties * to receive all properties.
beth.nolanCheck the properties of the account.Title
PS C:\Users\david.cook> Get-ADUser -Identity beth.nolan -Server za.tryhackme.com -Properties Title
DistinguishedName : CN=beth.nolan,OU=Sales,OU=People,DC=za,DC=tryhackme,DC=com
Enabled : True
GivenName : Beth
Name : beth.nolan
ObjectClass : user
ObjectGUID : c4ae7c4c-4f98-4366-b3a1-c57debe3256f
SamAccountName : beth.nolan
SID : S-1-5-21-3330634377-1326264276-632209373-2760
Surname : Nolan
Title : Senior
UserPrincipalName :
A. Senior
Q2. What is the value of the DistinguishedName attribute of Annette Manning (annette.manning)?
Hint. Use Get-ADUser, remember to set -Properties * to receive all properties.
annette.manningCheck the properties of the account.DistinguishedName
PS C:\Users\david.cook> Get-ADUser -Identity annette.manning -Server za.tryhackme.com -Properties Distingu
ishedName
DistinguishedName : CN=annette.manning,OU=Marketing,OU=People,DC=za,DC=tryhackme,DC=com
Enabled : True
GivenName : Annette
Name : annette.manning
ObjectClass : user
ObjectGUID : 57069bf6-db28-4988-ac9e-0254ca51bb2f
SamAccountName : annette.manning
SID : S-1-5-21-3330634377-1326264276-632209373-1257
Surname : Manning
UserPrincipalName :
A. CN=annette.manning,OU=Marketing,OU=People,DC=za,DC=tryhackme,DC=com
Q3. When was the Tier 2 Admins group created?
Hint. Use Get-ADGroup, remember to set -Properties * to receive all properties. Answer should be in DD/MM/YYYY HH:MM:SS AM/PM format. If you remote from your own local machine and it is in a timezone other than UTC+0 you will have to take timezones into account.
Tier 2 AdminsCheck the properties of the group.Created
PS C:\Users\david.cook> Get-ADGroup -Identity "Tier 2 Admins" -Server za.tryhackme.com -Properties created
Created : 2/24/2022 10:04:41 PM
DistinguishedName : CN=Tier 2 Admins,OU=Groups,DC=za,DC=tryhackme,DC=com
GroupCategory : Security
GroupScope : Global
Name : Tier 2 Admins
ObjectClass : group
ObjectGUID : 6edab731-c305-4959-bd34-4ca1eefe2b3f
SamAccountName : Tier 2 Admins
SID : S-1-5-21-3330634377-1326264276-632209373-1104
A. 2/24/2022 10:04:41 PM
Q4. What is the value of the SID attribute of the Enterprise Admins group?
Hint. Use Get-ADGroups, remember to set -Properties * to receive all properties.
Enterprise AdminsCheck the properties of the group.SID
PS C:\Users\david.cook> Get-ADGroup -Identity "Enterprise Admins" -Server za.tryhackme.com -Properties SID
DistinguishedName : CN=Enterprise Admins,CN=Users,DC=za,DC=tryhackme,DC=com
GroupCategory : Security
GroupScope : Universal
Name : Enterprise Admins
ObjectClass : group
ObjectGUID : 93846b04-25b9-4915-baca-e98cce4541c6
SamAccountName : Enterprise Admins
SID : S-1-5-21-3330634377-1326264276-632209373-519
A. S-1-5-21-3330634377-1326264276-632209373-519
Q5. Which container is used to store deleted AD objects?
Hint. Use Get-ADDomain and review the information
za.tryhackme.comVerify the properties of the domain.DeletedObjectsContainer
PS C:\Users\david.cook> Get-ADDomain -Server za.tryhackme.com
ChildDomains : {}
ComputersContainer : CN=Computers,DC=za,DC=tryhackme,DC=com
DeletedObjectsContainer : CN=Deleted Objects,DC=za,DC=tryhackme,DC=com
A. CN=Deleted Objects,DC=za,DC=tryhackme,DC=com
Task6
Q1. What command can be used to execute Sharphound.exe and request that it recovers Session information only from the za.tryhackme.com domain without touching domain controllers?
A. Sharphound.exe –CollectionMethods Session –Domain za.tryhackme.com –ExcludeDCs
Q2. Apart from the krbtgt account, how many other accounts are potentially kerberoastable?
Hint. Use the Per-Built Analytics Queries.
Sharphound.exeand run it.
PS C:\Users\andrea.mitchell> copy C:\Tools\Sharphound.exe ~\Documents\
PS C:\Users\andrea.mitchell> cd ~\Documents\
PS C:\Users\andrea.mitchell\Documents> .\Sharphound.exe --CollectionMethods All --Domain za.tryhackme.com --ExcludeDCs
At the end of the process, a ZIP file will be created.
PS C:\Users\andrea.mitchell\Documents> dir
Directory: C:\Users\andrea.mitchell\Documents
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 1/31/2025 3:44 PM 121297 20250131154447_BloodHound.zip
-a---- 3/16/2022 5:19 PM 906752 Sharphound.exe
-a---- 1/31/2025 3:44 PM 359470 YzE4MDdkYjAtYjc2MC00OTYyLTk1YTEtYjI0NjhiZmRiOWY1.bin
Download the ZIP file with the SCP command.
$ scp andrea.mitchell@THMJMP1.za.tryhackme.com:C:/Users/andrea.mitchell/Documents/20250131154447_BloodHound.zip .
andrea.mitchell@thmjmp1.za.tryhackme.com's password:
20250131154447_BloodHound.zip 100% 118KB 59.2KB/s 00:02
neo4j, and log in.bloodhound
$ sudo neo4j console
$ bloodhound
bloodhoundUpload the ZIP file by dragging and dropping it to the GUI.
AnalysisVerify your account from .List all kerberoastable Accounts

A. 4
Q3. How many machines do members of the Tier 1 Admins group have administrative access to?
Hint. Search for the Tier 1 Admins group and enumerate its information.
Tier 1 AdminsCheck from the group.Node InfoLocal ADMIN RIGHTS
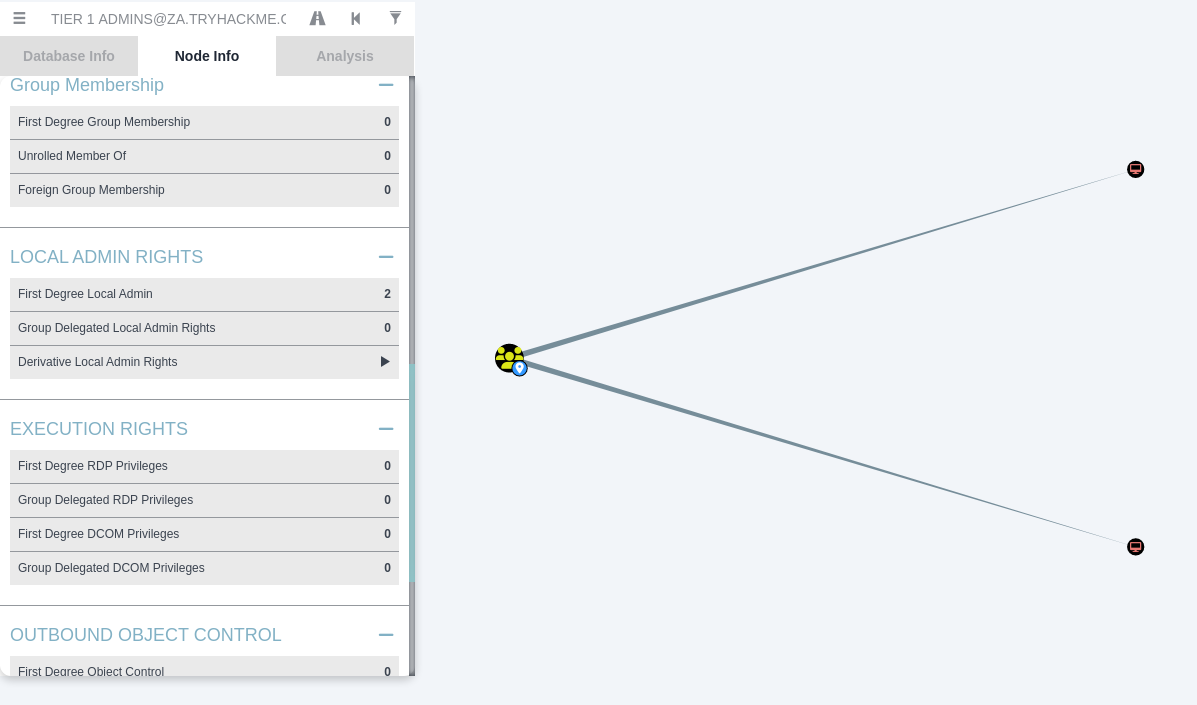
A. 2
Q4. How many users are members of the Tier 2 Admins group?
Hint. Search for the Tier 2 Admins group and enumerate its information.
Tier 2 AdminsCheck from the group.Node InfoGROUP MEMBERS

A. 15