This is a Walkthrough of TryHackMe “OWASP Top 10 – 2021”.

Task4
Q2. Deploy the machine and go to http://MACHINE_IP – Login with the username noot and the password test1234.
Launch the target machine, visit the website, and you will see a login form.
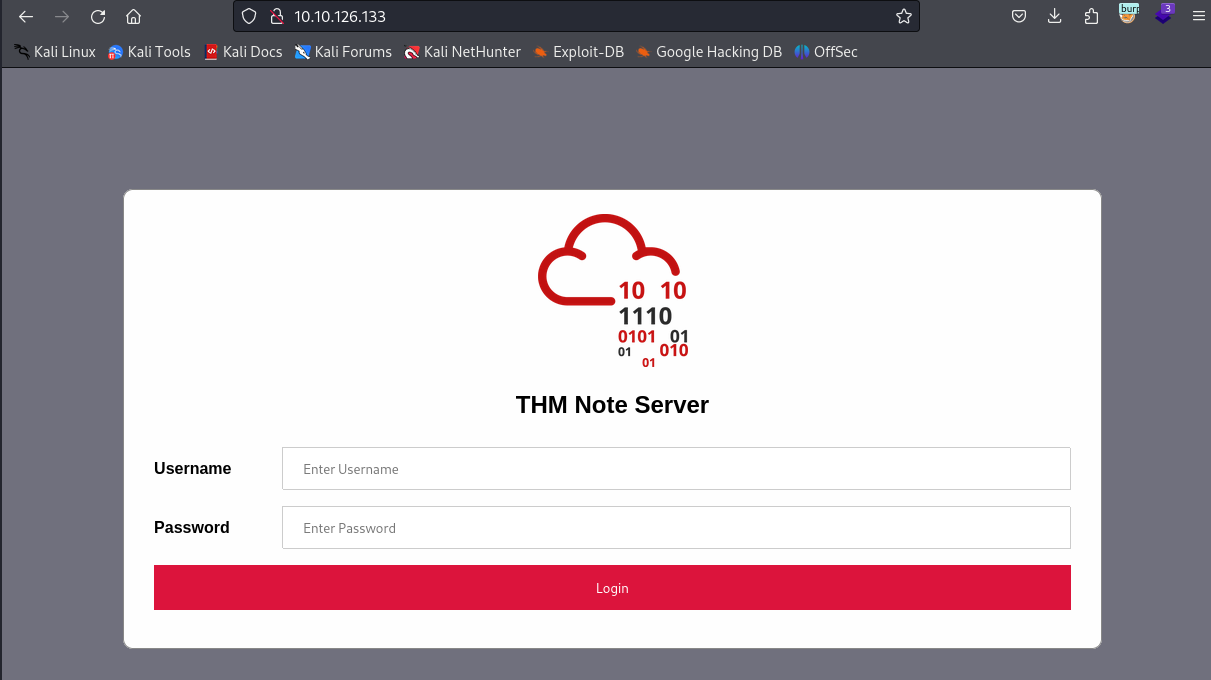
Username: nootLog in with ,.Password: test1234

Q3. Look at other users’ notes. What is the flag?
Hint. The URL contains ?note_id=1 – I wonder what happens if you change the parameter value? You might be able to access another user’s notes.
note_id=1It seems that the note with the number specified in the parameter will be displayed as follows.note_id
note_id=0You can get another note data by specifying and you get the flag.

A. flag{fivefourthree}
Task8
Q1. What is the name of the mentioned directory?
Hint. Have a look at the source code on the /login page.
81Access the number port.

/login.phpI found the path in the source code of ./assets

A. /assets
Q2. Navigate to the directory you found in question one. What file stands out as being likely to contain sensitive data?
/assetsI found access to thewebapp.db
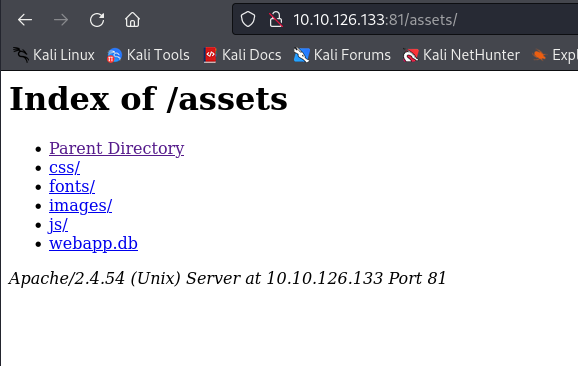
A. webapp.db
Q3. Use the supporting material to access the sensitive data. What is the password hash of the admin user?
webapp.dbWhen I downloaded and checked the data, I found the account name and password hash value.

A. 6eea9b7ef19179a06954edd0f6c05ceb
Q4. What is the admin’s plaintext password?
Hint. Read the supporting material.
The following site is used to analyze the hash value.
adminThe password hash was successfully parsed, and the plaintext of the password was known.

A. qwertyuiop
Q5. Log in as the admin. What is the flag?
/login.phpI was able to get the flag when I logged in with .Username: adminPassword: qwertyuiop

For the purposes of 1C0 THM{Yzc2YjdkMjE5N2VjMzNhOTE3NjdiMjdl}
Task10
Q1. What strange text file is in the website’s root directory?
82Access the number port.
$()Command injection was successful.
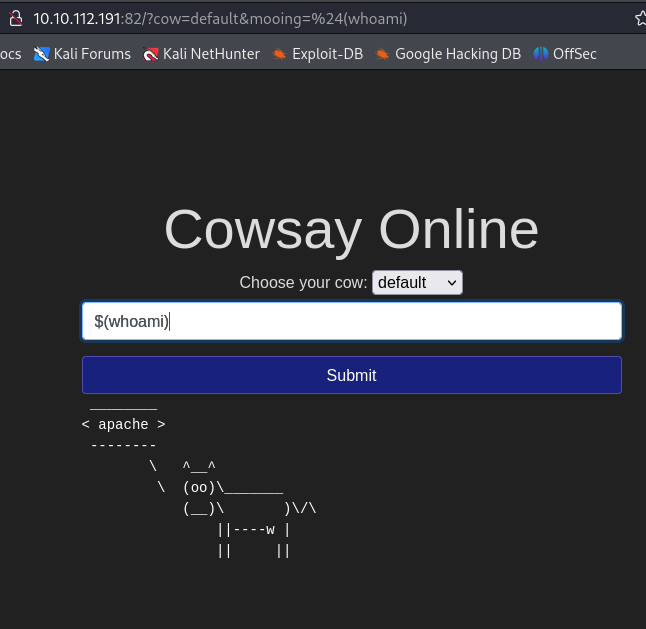
$(ls)I was able to check the file structure in .

A. drpepper.txt
Q2. How many non-root/non-service/non-daemon users are there?
/etc/passwdConfirm.

A. 0
Q3. What user is this app running as?
whoamiConfirm with the command.

A. apache
Q4. What is the user’s shell set as?
/etc/passwdConfirm from:
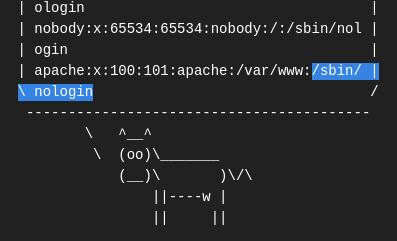
A. /sbin/nologin
Q5. What version of Alpine Linux is running?
Hint. The version can be found in “/etc/alpine-release”.
/etc/alpine-releaseConfirm from:

A. 3.16.0
Task11
Q2. What is the value of the flag in joseph’s account?
Hint. Is there any security question that can be easily guessed?
85Access the number port.

josephI don’t know the password for , so I will try to change the password from there./resetpass1.php

There are three secret questions, but it seems easy to guess from.favorite color
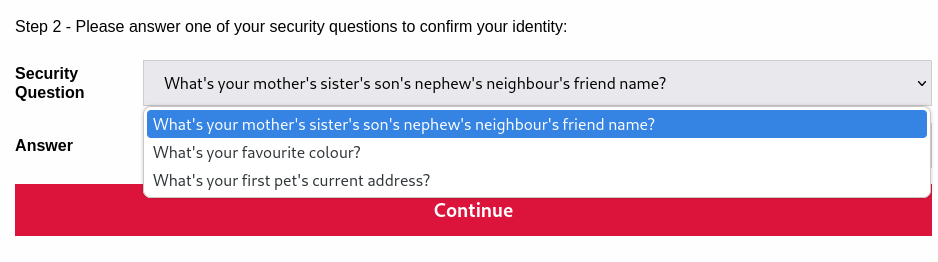
When you finally enter it, you will be issued a new password, so make a note of it.green
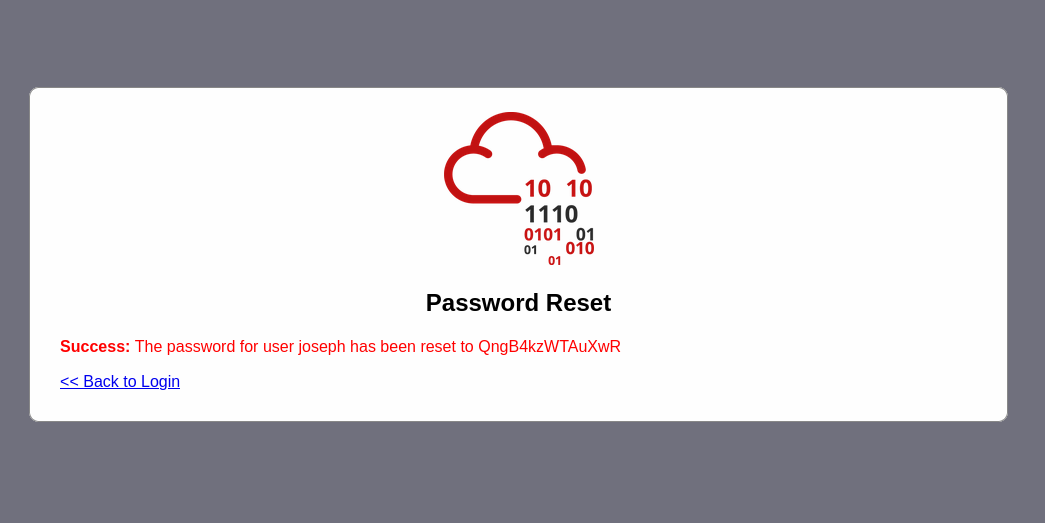
You have successfully logged in with your new password.
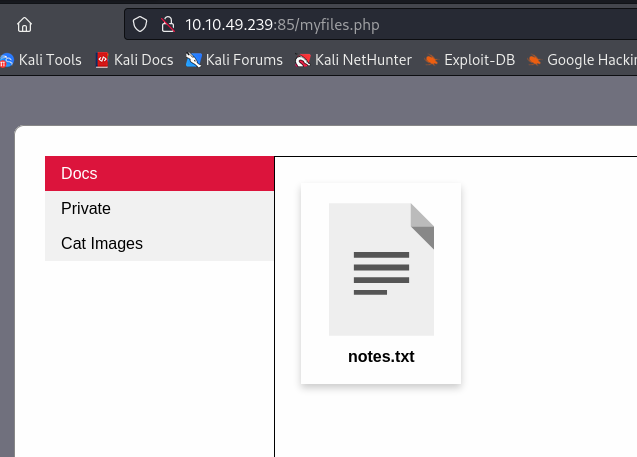
I was able to get the flags from a text file.
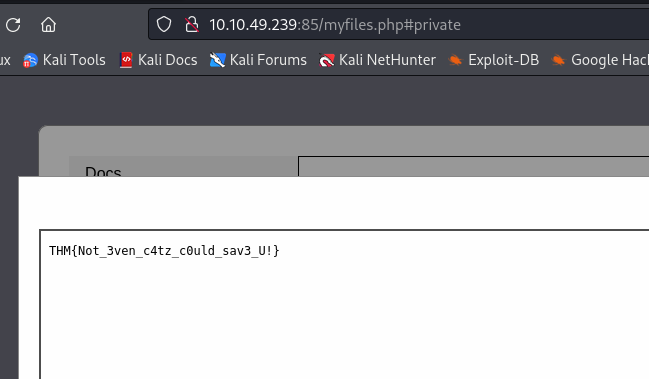
A. THM{Not_3ven_c4tz_c0uld_sav3_U!}
Task12
Q1. Navigate to http://TARGET_IP:86/console to access the Werkzeug console.
/consoleWhen I accessed the Werkzeug console, I was able to see the Werkzeug console.

Q2. What is the database file name (the one with the .db extension) in the current directory?
osRCE from the console was successful with the help of the module.
import os; print(os.popen("ls -l").read())

A. todo.db
Q3. Modify the code to read the contents of the app.py file, which contains the application’s source code. What is the value of the secret_flag variable in the source code?
Hint. The flag looks like THM{…}. Be sure to write it without the surrounding quotes!
app.pyReview the code.
import os; print(os.popen("cat app.py").read())

A. THM{Just_a_tiny_misconfiguration}

